技术篇:首届硅谷 GrinCon 上关于 Grin 的一手干货
原文标题:《关于首届硅谷 GrinCon 你想知道的一切(上篇)》
p.s 因为是英文会议,为了更精准的表述,有些内容将保留英文。
作为 Grin 上线后在美国的第一场会议,现场吸引了非常多的开发者和对 Grin 感兴趣的成员。金氪资本参加了本次大会,并为市场带来关于近期热门 Grin 的一手干货,由于整场会议的内容十分丰富,所以文章将分为上、下两篇。 上篇主要分享 Grincon 关于技术的讨论,下篇着重于挖矿和投资方面的介绍。
GrinCon 的开始
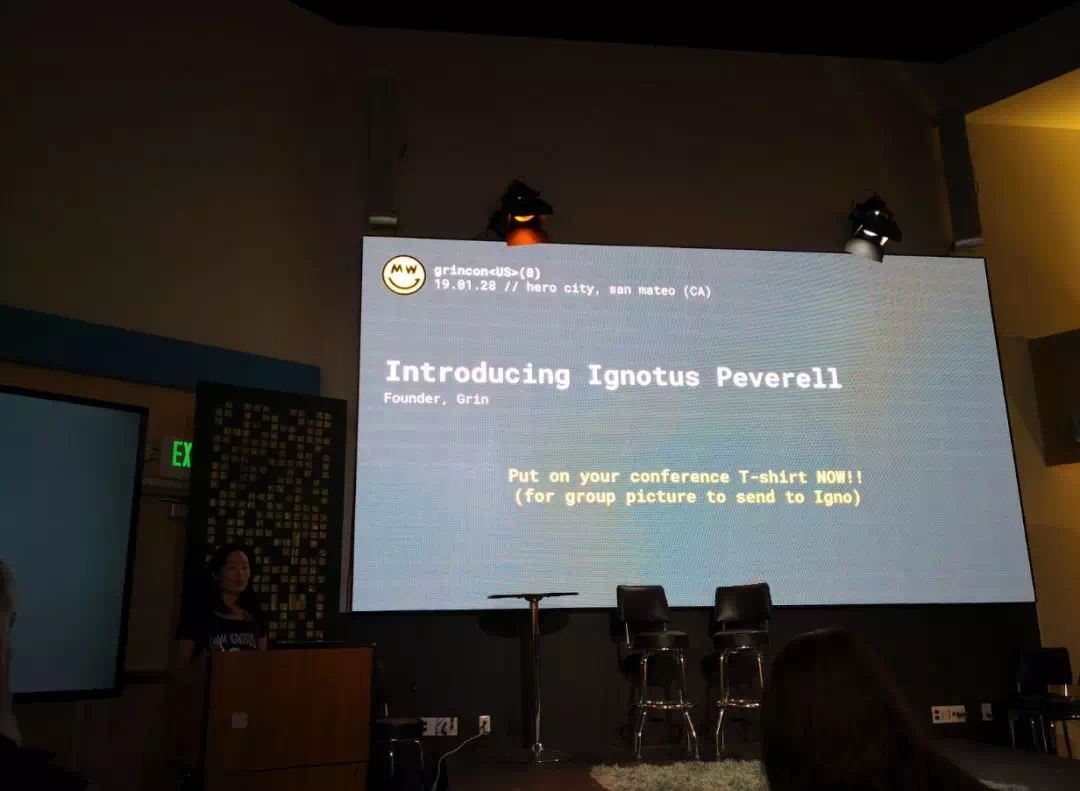
Grin 的创始人 Ignotus Peverell 通过处理过的机器人语音谈话启动了会议,所以不知道究竟是男是女,充满了神秘感。
Ignotus Peverell 是个化名,出自哈利·波特故事其中《三兄弟的传说》中的一个人物,作为三兄弟中最小的一个,Ignotus 是三个人里面最谦虚、也是最聪明的一个。也正因为这些品质,他最终从死神狡猾的计划中活了下来。他得到的第三件死亡圣器「一件隐形衣」,在后代中代代相传,成为波特家族的传家宝,并最终传到哈利·波特的手中。
拥有隐形衣这个特点,正像是隐私货币的特性。非常有意思的取名。
来自 Blockcypher 的 Catheryne 接着介绍了 Grin 的几个特点:

Daniel Lehnberg introduces MW. Overview of Grin for Layperson
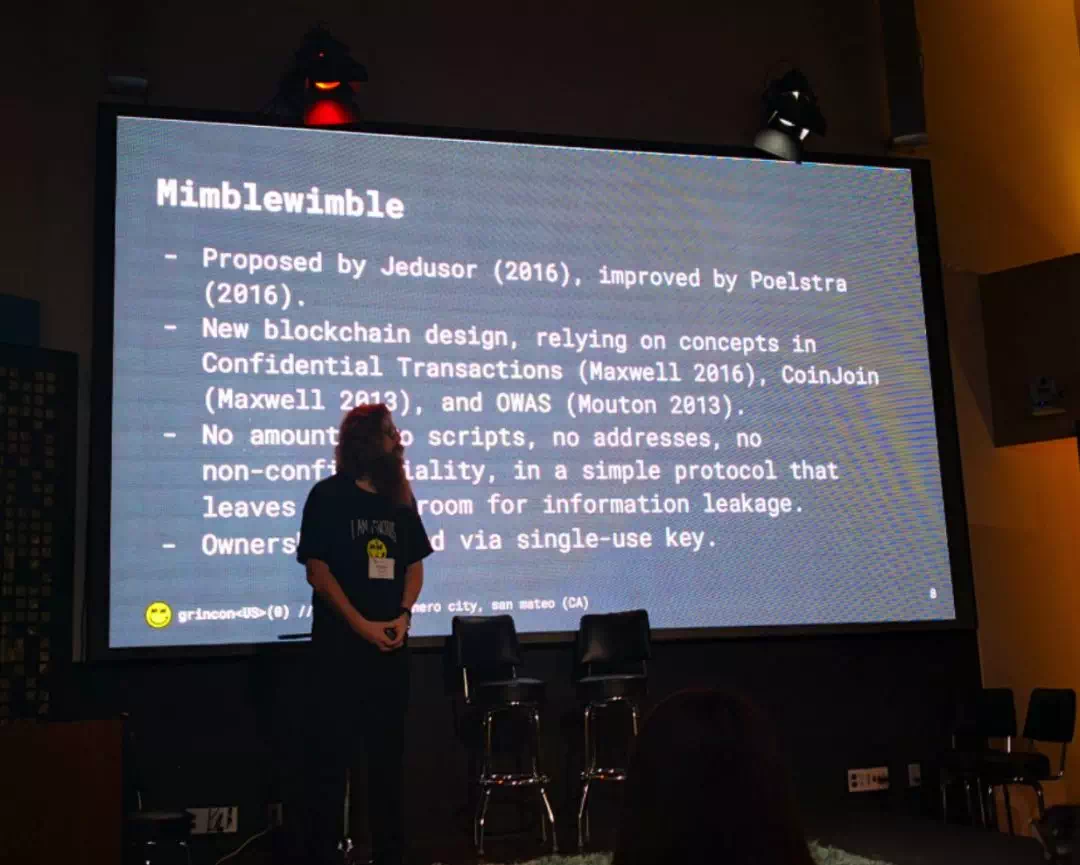
MinmbleWimble,也来源于「哈利波特」, 是一道咒语,意为结舌咒 - 可以让人舌头打结。
Mimblewimble 的首次亮相是在「哈利·波特」系列的第二部《哈利波特与密室》,在决斗俱乐部中,霍格沃茨黑魔法教授吉德罗,希望教会学生们预防蛇怪 Basilisk 的攻击,使出了结舌咒「Mimblewimble」
John Woeltz on the security audit of Grin. Grin Crypto Security Audit Results

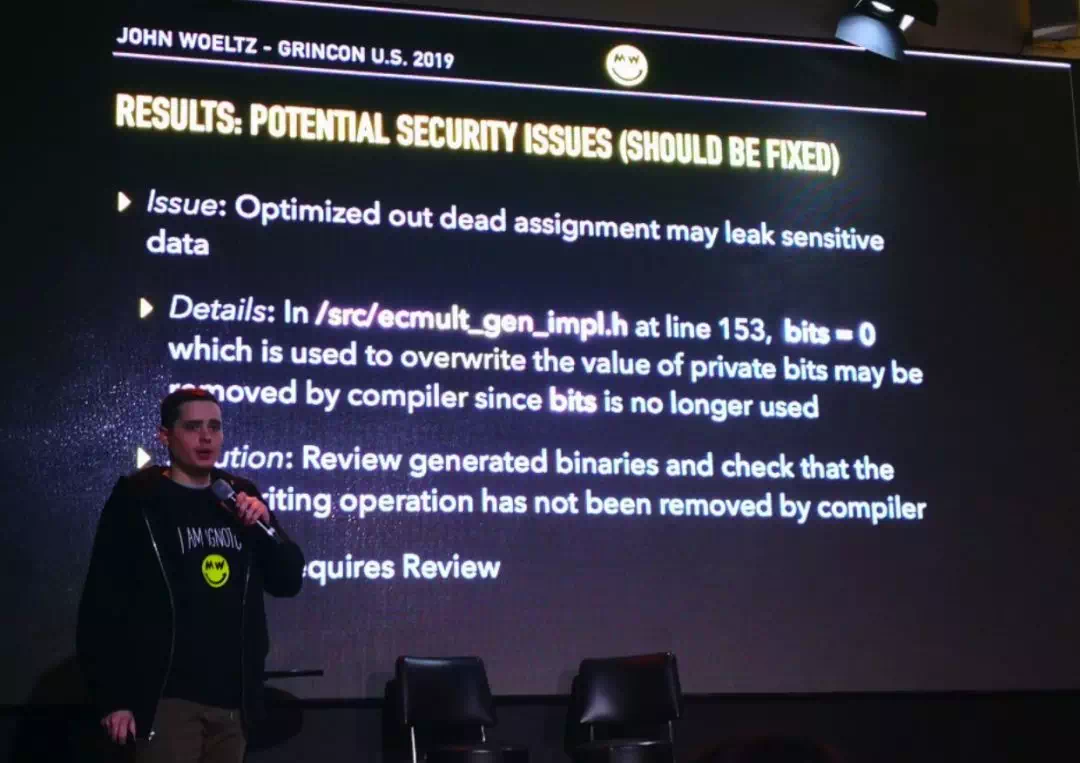
他描述了 GRIN 在审计方面的障碍。因为时间和预算的限制,现在审计的范围仅限于加密库。
IIRC dalek-crypto 有更好的基准,但选择了 libsec256k1。
现在加密库已经审计过,之后团队还会审计更多的代码。
Grin 他们需要 5.5 万欧元来完成剩余代码审计。费用相对较少,这是 Solidity 审计公司对这些较简单代码的审计收费。
Next up, Michael Cordner Grin Privacy and Scalability
一张幻灯片描述完 MW,介绍了 Grin 在 Privacy & Scalability 方面的特性和存在的挑战。
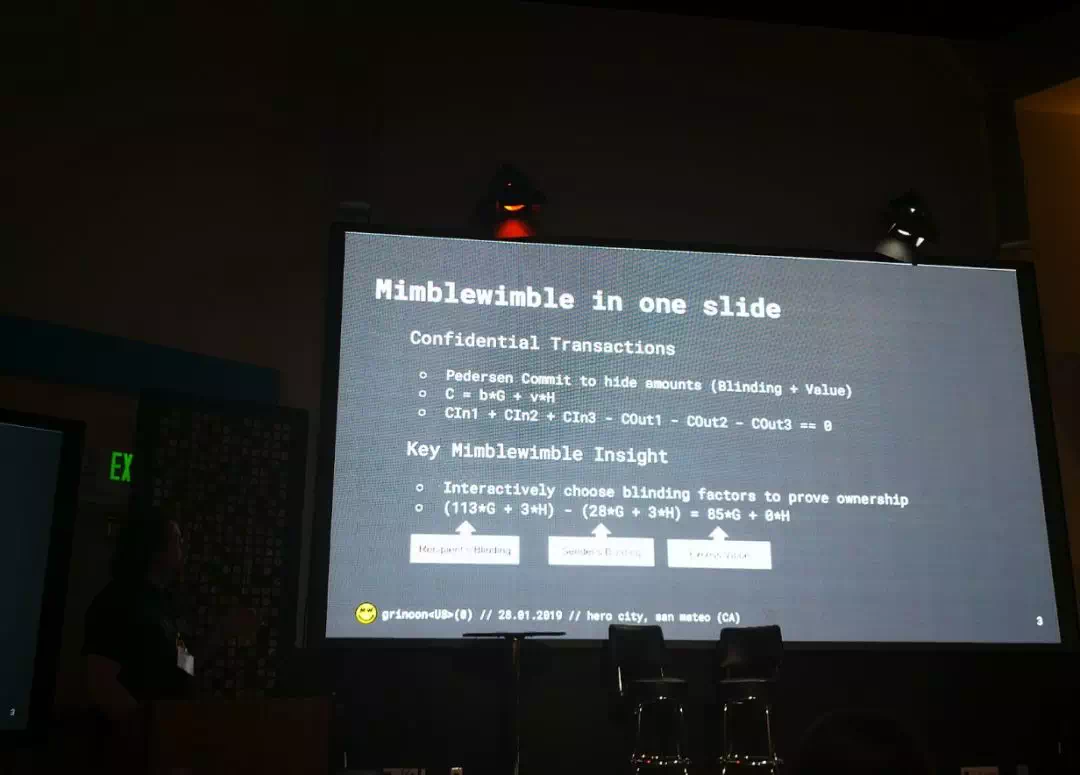
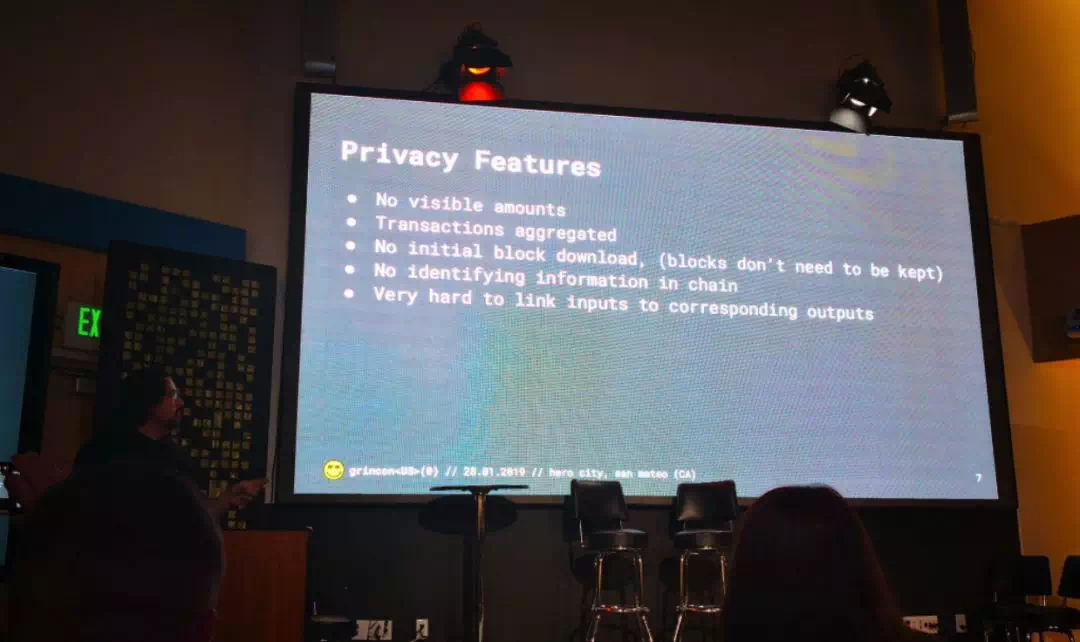
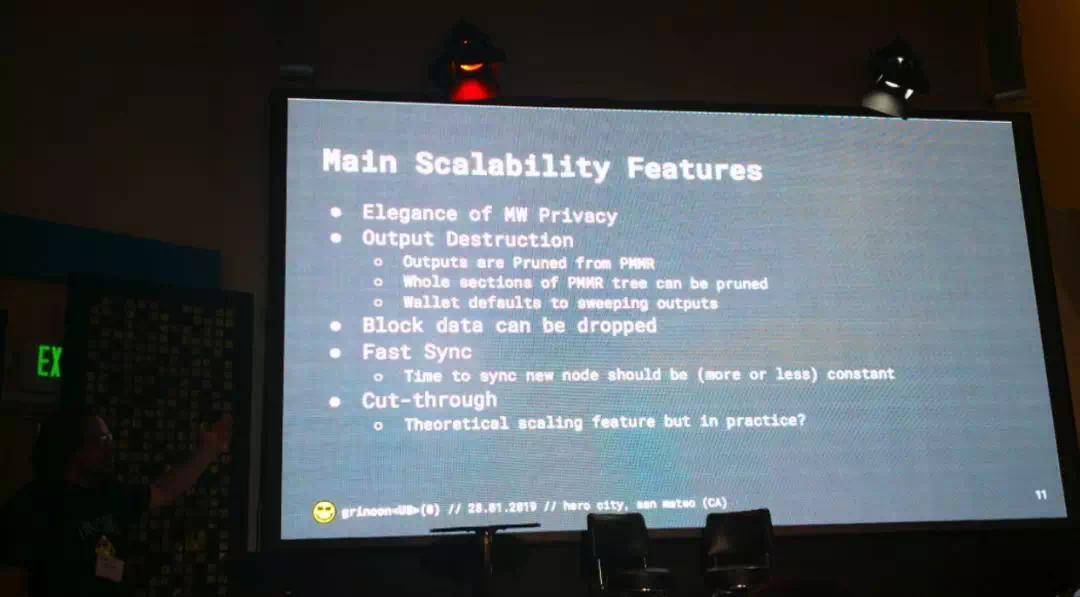
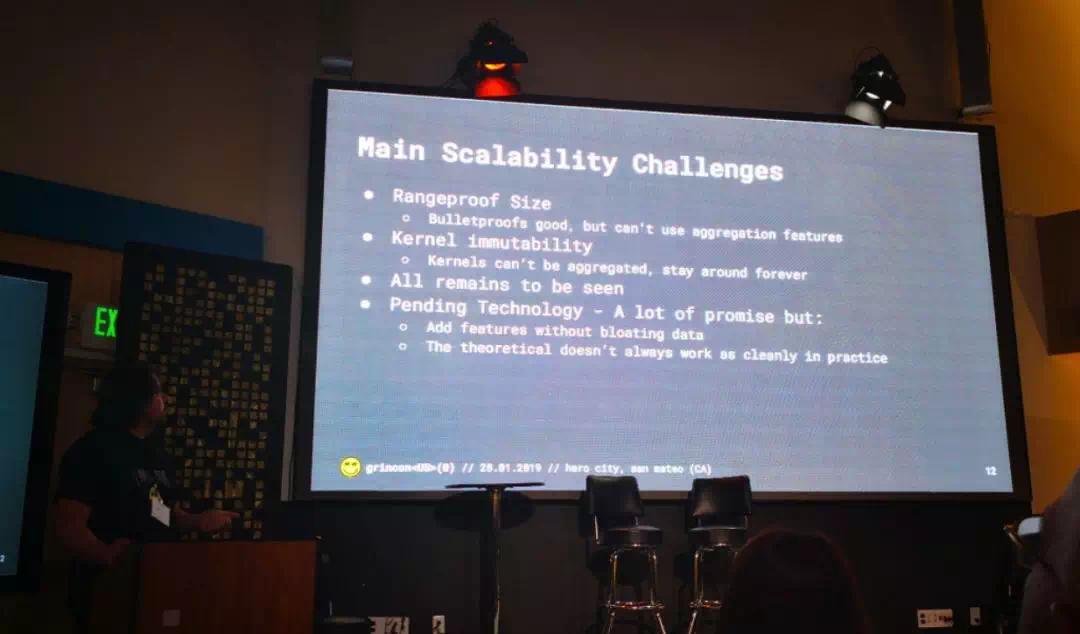
Fireside Chat with Dan Boneh
Mimblewimble & PostQuantum Cryptography for Privacy Coins.
-Dan Boneh discussed post quantum crypto:
Imagine if Moore's law applied to QC. You need about 100m 'physical' qubits (with the consideration of error correction, as the quibts are not pure). Log_18(100m) is about 30 years until we start to see meaningful impact.
- For post Quantum Crypto\, Cryptography will on a classical computer that is secured even when adversary has a quantum computer
- Hash based, too big (30KB, ECDSA are 64 bytes), useful for software updates
- Lattice based (1KB, no good algo for them, look up SIS)
- Isogeny based (10KB, group actions instead of groups).
As a result, there’s clear need for post quantum signature that is similar to size/usability as ECDSA as well as more efficient accumulators than Merkle Trees. RSA Accumulators much better, but are based on groups of groups of unknown order which are not.
- Post quantum Verifiable Delay Functions?
Also built from groups of unknown order. Not post quantum secure.
Who knows? They don't, yet! They're working on it.
He’s view on PoW is that:
-「Hopefully in 30 years we will move away from Proof of Work」.
- Difficulty will adjust exponentially\, which is not necessarily a bad thing considering how much money would Bitmain would be forced to spend lolll.
- However\, This scenario is likely to take longer\, due to the noisy qubits and the error correction. As engineering improves\, noise will go down and may eventually become a threat.
When being asked what features would he put in a new cryptocurrency if he created one, he mentioned:
- Signature Aggregation
- Privacy via ZK
- Efficient Consensus (without burning a lot of energy)

I love this industry! Paraphrasing #AndrewPoelstra: 「We think this is impossible now... But then again, most of the things we have today were thought to be impossible a few years ago」 #grinning
Grin 的钱包和 Infrastructure 相关项目:
Wallets and Infrastructure for Grin:

RSA Accumulators
——Benedikt Bünz
He addressed the work published in Batching Techniques for Accumulators with Applications to IOPs and Stateless Blockchains.
The paper explains how we can construct proofs of (non-)membership as well as batch them across multiple blocks.
「A cryptographic accumulator is a primitive that produces a short binding commitment to a set of elements together with short membership/non-membership proofs for any element in the set.」
Examples of Accumulators include:
- Merkle Tree
- RSA Accumulators
- Pairing-based Accumulators
He first introduced how RSA Accumulators work and its advantages:
-「Proving membership of an element in an accumulator requires revealing the value of the element, and a witness.」
-「The proof of non-membership requires calculating Bezout’s Coefficients of the element we’re proving and the product of the elements in the set. 」
The positives include: Constant size inclusion proofs, Dynamic stateless adds, and decentralized storage.
While there’s still room for improvement.
He then addressed the Batching techniques for accumulators with applications to IOPs and Blockchains:
- Key concepts include:
-Batching: Batch verify n proofs faster than verifying a single proof n times
-Aggregating: Aggregate n membership roofs in a single constant size proof
「These accumulators can be used to create stateless blockchains, in which nodes do not need to store the whole state to be convinced about which blocks are valid.」
With the introduction of Proof of Exponentiation, which allows fast block verification and fast full-sync verification, works will be shifted from miners to users and distributed storage will be achieved.
The Original Paper can be found here: https://eprint.iacr.org/2018/1188
With a nice review here: https://blog.goodaudience.com/deep-dive-on-rsa-accumulators-230bc84144d9
Cucka(r)(t)oo Mining Proof-of-Work
——John Tromp
John first briefly reviewed the concept of Proof-of-Work:
PoW is used to achieve The characteristics of PoW include:
- Hard to Solve
- Easy to Verify
- Tied to some messages
Then he introduced Hashtable, the history of Cuckoo Hashtable and how it works:
-「Cuckoo Cycle aims to be an ‘egalitarian’ proof-of-work, that is, to minimize performance-per-dollar differences across hardware architectures, and make mining—the process of looking for proofs—on commodity hardware cost-effective.」
-「This is to be achieved by making main memory latency a bottleneck, since DRAM latencies have remained relatively stable while cpu-speed and memory bandwidth vary highly across hardware architecture and process technology」
-「A Cuckoo hashtable consists of two same-sized tables each with its own hash function mapping a key to a table location, providing two possible locations for each key」
-「Upon insertion of a new key, if both locations are already occupied by keys, then one is kicked out and inserted in its alternate location, possibly displacing yet another key, repeating the process until either a vacant location is found, or some maximum number of iterations is reached. The latter is bound to happen once cycles have formed in the Cuckoo graph.」
Later he addressed Cycle-finding:
The Cuckoo miner finds the cycle base, it emulates the cuckoo hashtable. Which is memory efficient, uses 64 bits per edge, but with high latency.
The Graph Miner finds all cycles, it searches the graph from edge onward to see if there’s a cycle. It uses 192 bits per edge.
As well as trimming:
- The Edge-Trimming is a process that 「repeatedly identify nodes of degree one and eliminate their incident edges.」 The resulting un-trimmable edges form a cycle.
-「For Grin, it takes thousands of trimming rounds to get to the cycle. Once you get close, you can switch to another algorithm.」
And then briefly touched the mining issue:
For GPU Mining it’s Cuckaroo on 2^29 edges, which takes 5.5GB of memory, and tweaked every 6 months to maintain ASIC resistance.
For CPU Mining it’s Cuckatoo on 2^31 or more edges, which takes 512MB of memory
The original Paper can be found here: https://eprint.iacr.org/2014/059.pdf
Grin 的未来,项目路线图
——Michael Cordner
When talking about the product’s roadmap, it’s funny that they showed a pic like this:

The general goal including: provide open, scalable privacy for all; Further MW Research, Development and Testing; Ensure Grin/ MW is accessible and usable for all needs.
In order to achieve this, Igno said the following are needed:
- Ongoing improvements to what’s there
- Calm and measured introduction of New Features
- Enhancement and Extension to support the community
The future techs includes:
- Atomic Swaps, Relative Locks, FlyClient, Dandelion++ for the near future, and
- Vaults/Covenants, RSA Accumulators, Scriptless Scripts, 2nd Tier Enablement for a little bit later.
Besides, continued support are very much needed from the community, especially from the API side:
- Transaction building APIs
- Wallet APIs
- Keychain APIs
- Node APIs
- Mobile/Web/Native/Cloud etc
The current governmental structure seems to work… for now, but might be subject to change in the future.
Last but not the least, continued support are also needed from the funding side and please take note to this website:

总结
Grincon 在技术方面的分享非常 Hard Core,如果非技术人士,恐怕难以理解其中的奥妙。 作为 Grin 爱好者,看到这样的技术社区是非常喜悦的一件事,Grin 整个项目都崇尚开源社区文化,积极拥抱各类形式的开发者与它们合作。
如果你不是技术人员,那 Grincon 下篇关于挖矿与投资方面的内容,也许更适合你阅读,敬请期待。
参考资料:
https://www.notion.so/Grincon-Notes-9d76e5bfbf494a33bdb9b7cf8d8303c8
免责声明:
1.本文内容综合整理自互联网,观点仅代表作者本人,不代表本站立场。
2.资讯内容不构成投资建议,投资者应独立决策并自行承担风险。
-
error
